Understanding Post-Quantum Security: What Business Leaders Need to Know
The cybersecurity landscape is approaching a fundamental shift. While quantum computers remain largely experimental today, their eventual capability to break current encryption methods represents a significant concern for organisations handling sensitive data. This article examines the nature of this challenge and what it means for business security planning.
The Quantum Computing Difference
Quantum computers operate on fundamentally different principles than conventional computing systems. Rather than representing an incremental improvement in processing power, they employ quantum mechanical phenomena to solve specific types of mathematical problems with unprecedented efficiency.
Currently, quantum computers lack the capability to threaten established cryptographic systems. However, ongoing development suggests this limitation may not persist indefinitely. The timeline remains uncertain, with estimates ranging from several years to multiple decades, though major technology companies are planning for transitions within the next ten years.
The Cryptographic Challenge
The concern centres primarily on public key cryptography, which underpins much of modern digital security. This technology enables:
- Digital signatures that verify authenticity and integrity
- Secure communication protocols including HTTPS
- Email security through standards such as PGP and S/MIME
- Authentication systems for identity verification
- Secure establishment of encryption keys
An algorithm developed by mathematician Peter Shor demonstrates that sufficiently powerful quantum computers could reverse the mathematical operations protecting data encrypted with public key methods. This theoretical capability, while not yet practically achievable, has prompted forward-looking security planning.
Symmetric key cryptography, used for encrypting stored data and securing communications through VPNs and web browsing, faces a comparatively modest increase in vulnerability through a different quantum algorithm developed by Lov Grover.
Business Implications
The potential impacts of quantum-capable decryption include:
- Compromise of authentication credentials
- Forgery of digital signatures
- Decryption of previously secured data
The significance of these scenarios varies considerably by organisation. For some entities, exposure of historical data may present minimal concern. For others, particularly those handling long-term strategic information, government communications, or confidential business intelligence, the implications could be substantial.
The Present-Day Relevance
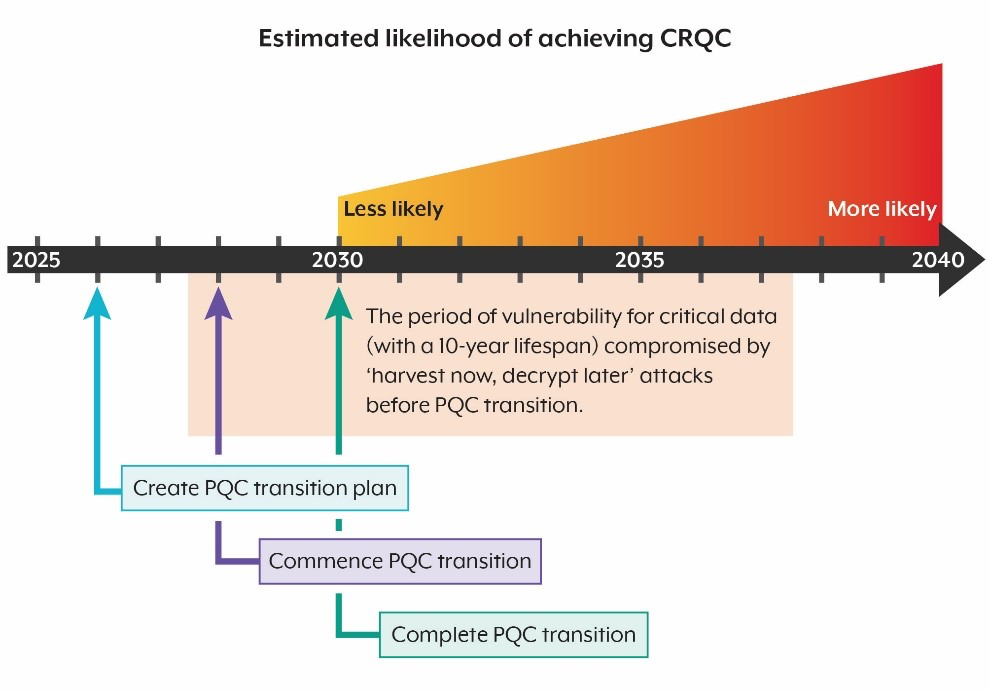
Given the uncertainty around quantum computing timelines, one might reasonably question why this warrants current attention. The answer lies in what security professionals term "harvest now, decrypt later" attacks.
Sophisticated threat actors may be collecting encrypted data today with the expectation of future decryption capability. This means that data protected by current encryption standards could potentially be vulnerable once quantum computers reach sufficient capability. Consequently, protecting today's sensitive information requires implementing quantum-resistant encryption methods now.
Practical Considerations
The energy requirements and operational complexity of quantum computers suggest that even once the technology matures, its use may remain largely confined to well-resourced actors, particularly nation states. However, this does not diminish the need for appropriate security measures, particularly for organisations whose threat models include state-level actors.
Industry Response
Major technology providers are actively addressing this challenge. IBM's quantum development roadmap projects full-scale quantum computing capability around 2033.
The National Institute of Standards and Technology (NIST) has approved quantum-resistant algorithms for deployment. Several prominent companies have begun implementation:
- GitHub has integrated quantum-resistant algorithms into their SSH key exchange systems
- Apple transitioned iMessage to quantum-resistant encryption in February 2024
- Microsoft and IBM are developing comprehensive quantum-safe solutions
Planning for Transition
For most organisations, the appropriate first step involves assessment rather than immediate action. This typically begins with developing a Cryptographic Bill of Materials (CBOM), which documents:
- Cryptographic algorithms currently in use
- Key management systems and certificates
- Protocol implementations
- Configuration details
This inventory enables organisations to understand their current cryptographic posture and identify which systems may require modification to address future quantum computing capabilities.
ASD has an excellent guide: Planning for post-quantum cryptography
The Broader Security Context
While quantum computing presents a specific challenge, it exists within the larger context of information security. Data that cannot be extracted from an organisation's systems cannot be decrypted, regardless of future technological capabilities. This reinforces the continuing importance of comprehensive security measures.
Current security practices remain essential. A data breach today may have implications extending a decade or more into the future, making robust security testing and infrastructure protection as critical as ever.
Conclusion
Post-quantum security represents an evolving challenge rather than an immediate crisis. The timeframe for quantum computers achieving cryptographically relevant capability remains uncertain, but prudent organisations are beginning to assess their exposure and plan accordingly.
For business leaders, the appropriate response involves understanding the nature of the challenge, maintaining awareness of industry developments, and ensuring that overall security posture remains strong. As with many security challenges, preparation and assessment prove more valuable than reactive measures.
At SilentGrid Security, our focus remains on helping organisations identify and address current vulnerabilities through rigorous adversary simulation and penetration testing. Strong security fundamentals today provide the foundation for addressing tomorrow's challenges, including those posed by advancing quantum computing capabilities.